HeroSecondaryQuote
JSS component is missing React implementation. See the developer console for more information.

In Part 1 of this series, we explored the definition of identity proofing, how it works, and some common use cases in banking, healthcare, government, and other industries. Today we’re taking a closer look at the many parts that make up a solution aimed at validating user identities and incorporating validation data into business processes.
Determining the right identity affirmation and ID proofing solution for your organization can be more complicated than it sounds (but it doesn’t have to be—more on that later). An effective solution encompasses an intricate ecosystem comprising an array of moving parts, all of which must integrate seamlessly to deliver the desired results. How you approach the various components can make a huge difference in the success of your solution and the time and effort required to implement and maintain it.
Read part 1: What Is Identify Proofing and Why It’s Only Part of the Solution
The complex identity proofing and affirmation ecosystem
Think about your car for a second. Sure, it’s a distinguishable object we call an “automobile,” but it’s also an amalgamation of many different systems: engine, ignition, fuel, exhaust, electrical, cooling, steering, and the list goes on. If even one system fails to work properly—or fails to integrate with the others—you may find yourself doing a lot of walking.
In much the same way, successful identity proofing and affirmation relies on the intricate coordination of many different components.
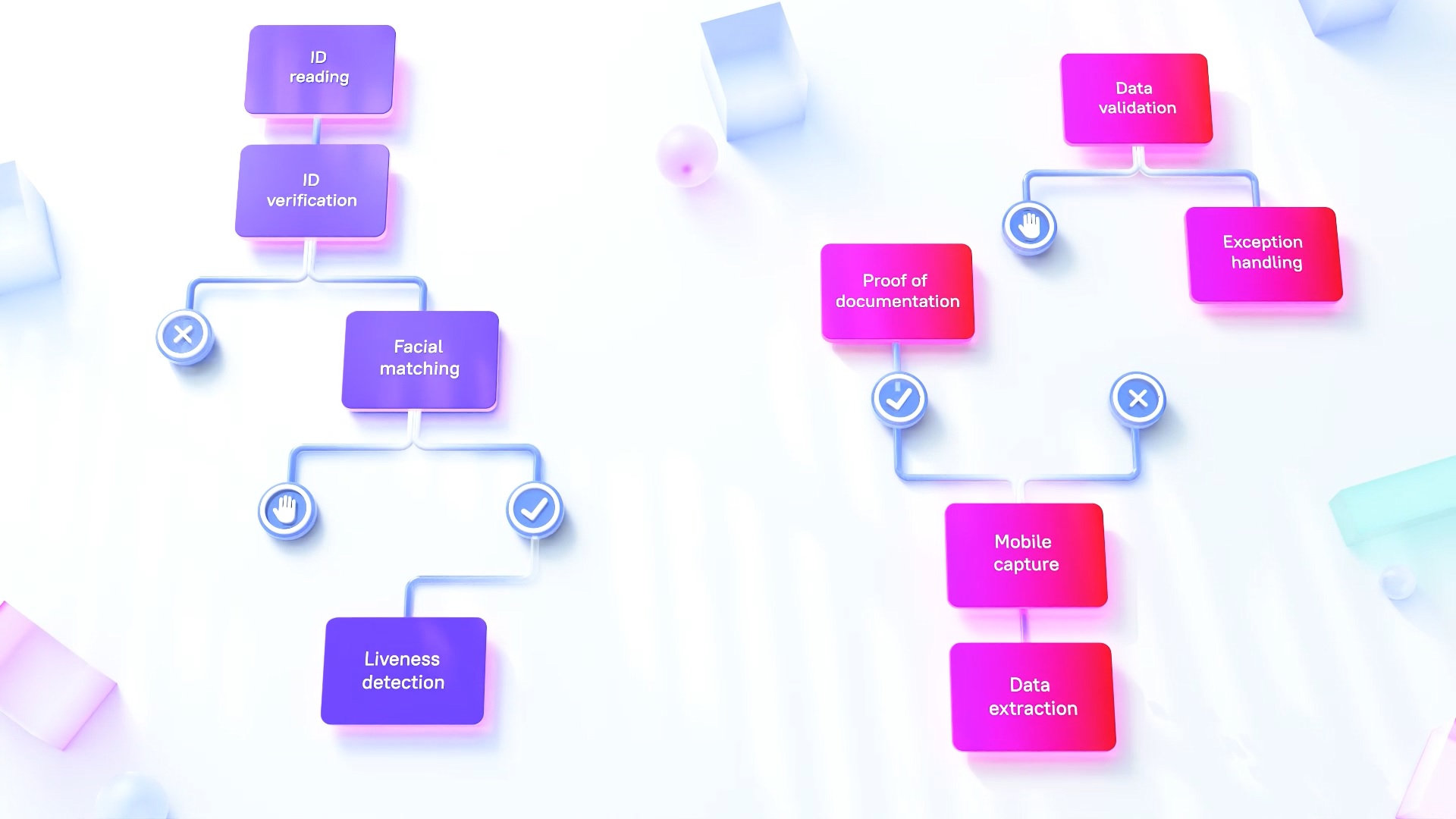
We’ve compiled a list of the most critical technologies and functions that must work together seamlessly to deliver optimal performance, no humans necessary:
ID reading
The first step in the proof-of-identity process is extracting data from identifying documents (ID)—driver’s license, passport, etc. Effective ID reading software processes both machine readable zones (MRZ, such as the long lines of characters and numbers on a passport) and human readable information to gather the necessary data.
ID verification
After the relevant data has been extracted, the identifying documents must be verified as authentic and unaltered. ID verification software verifies the layout, characteristics, and security features within the ID and can detect image tampering that indicates possible fraud.
Biometric authentication
Once the identifying documents have been analyzed and verified, the next step is to verify that these documents match the person making the request. With biometric authentication software, the user snaps a real-time mobile selfie that goes through a facial matching process to verify that the applicant matches the submitted documents. Additionally, it is critical to include liveness detection to ensure the person is alive, real, and not a photograph or fake.
Trailing documents
For complex procedures such as loan applications, additional documents such as utility bills and paycheck stubs are required. These documents require a process that’s separate from ID reading (see above) and focuses on specialized data extraction as well as affirmation that the data on the documents matches the applicant’s data.
Exception handling
Every standard procedure has its share of exceptions, and your proof of identity solution needs a way to handle them—either by handing off certain transactions to human workers or via a fully automated process.
Process intelligence and mining
The efficiency of your proof-of-identity processes is a key factor in the satisfaction of your customers and the smooth functioning of your operations. Process intelligence and mining lets you monitor how processes actually happen, compared with how they should execute, and correct any inefficiencies as they arise.
Dynamic fraud detection
Unfortunately, perpetrators of fraud are constantly coming up with new techniques. Your proof-of-identity solution needs to stay current with the latest red flags to help you identify and stop bad actors before they can do any damage.
Intelligent automation
Your proof-of-identity solution should be able to operate without human intervention (unless needed for certain transactions), allowing your human workers to focus their time and energy on interesting, more complex tasks.

Explore our webpage to learn more about ABBYY Proof of Identity.
Bringing it all together
As you begin researching the identity proofing and affirmation solutions available in today’s market, you’ll soon realize that relatively few vendors deliver the entire slate of capabilities you need. While you can take a piecemeal approach and implement separate solutions, this strategy can lead to more than its share of headaches. Not only will each platform need to be maintained according to its own update schedule, but integrating disparate solutions from disparate providers—and maintaining those integrations over time—can be a hassle. Also, determining which is the “best of breed” option in each individual category can be a time-consuming research project.
Working with a single vendor enables you to avoid the pitfalls of the piecemeal approach while offering additional advantages:
- You have one point of contact for any questions or issues that may arise with your platform.
- Integrations among the various functions are done for you behind the scenes to ensure seamless operation on a continuous basis.
- You only have to go through the vendor approval process once, instead of having to repeat it for every piece of the puzzle.
- The overall solution works better since it was designed to coordinate all elements to function together seamlessly, resulting in greater accuracy and effectiveness.
For help in making your selection, several analyst firms evaluate technology providers’ offerings, capabilities, strengths, and limitations to assist buyers in determining how to best meet their needs.
Discover why 10 top analyst firms have named ABBYY a leader this year.
A better way
Choosing a proof-of-identity solution is a decision that impacts your customers, your employees, and the secure functioning of your business processes—today and for years in the future. We’ve explored the many moving parts that go into this solution and the two overall approaches to implementing it. You can choose to select, implement, integrate, and maintain an array of different platforms from different providers, or you can work with a single vendor who does the demanding work for you. And when that vendor is a proven reliable partner like ABBYY, the right choice is obvious.
Subscribe for blog updates
RelevantBlogPosts
JSS component is missing React implementation. See the developer console for more information.
ConnectWithUs
JSS component is missing React implementation. See the developer console for more information.

